The Connective Platform
In today’s rapidly evolving digital landscape, organizations face an ever-increasing number of cyber threats.
To combat these risks, the Connective Platform goes beyond traditional security measures, providing a comprehensive and proactive approach to safeguarding sensitive data and critical systems.
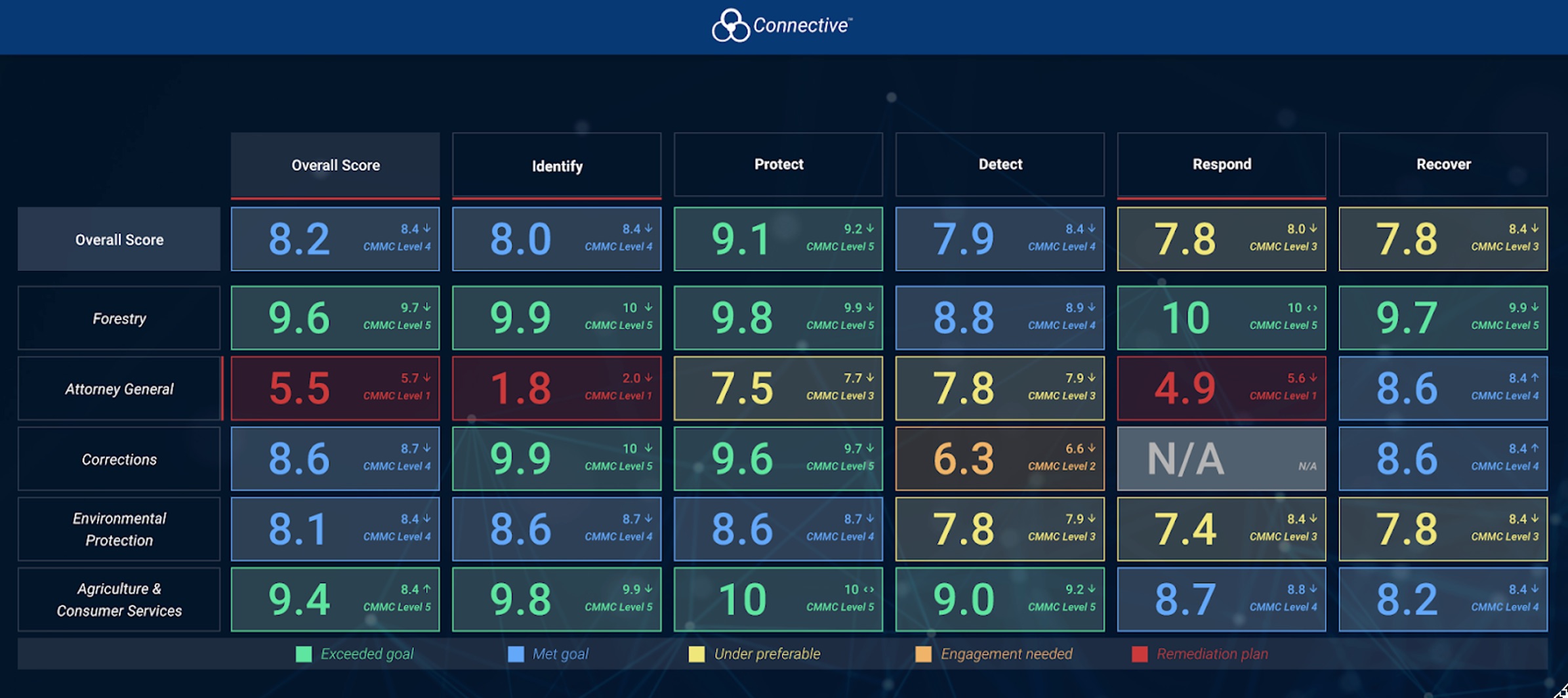
One of the key advantages of the Connective Platform is its user-friendly and auditable dashboard. This intuitive interface provides comprehensive visibility into an organization’s cybersecurity program, enabling security leaders and executives to make informed decisions and monitor the effectiveness of their security measures. With customizable reporting features and real-time analytics, stakeholders can easily track security posture, identify vulnerabilities, and measure the success of risk mitigation efforts.
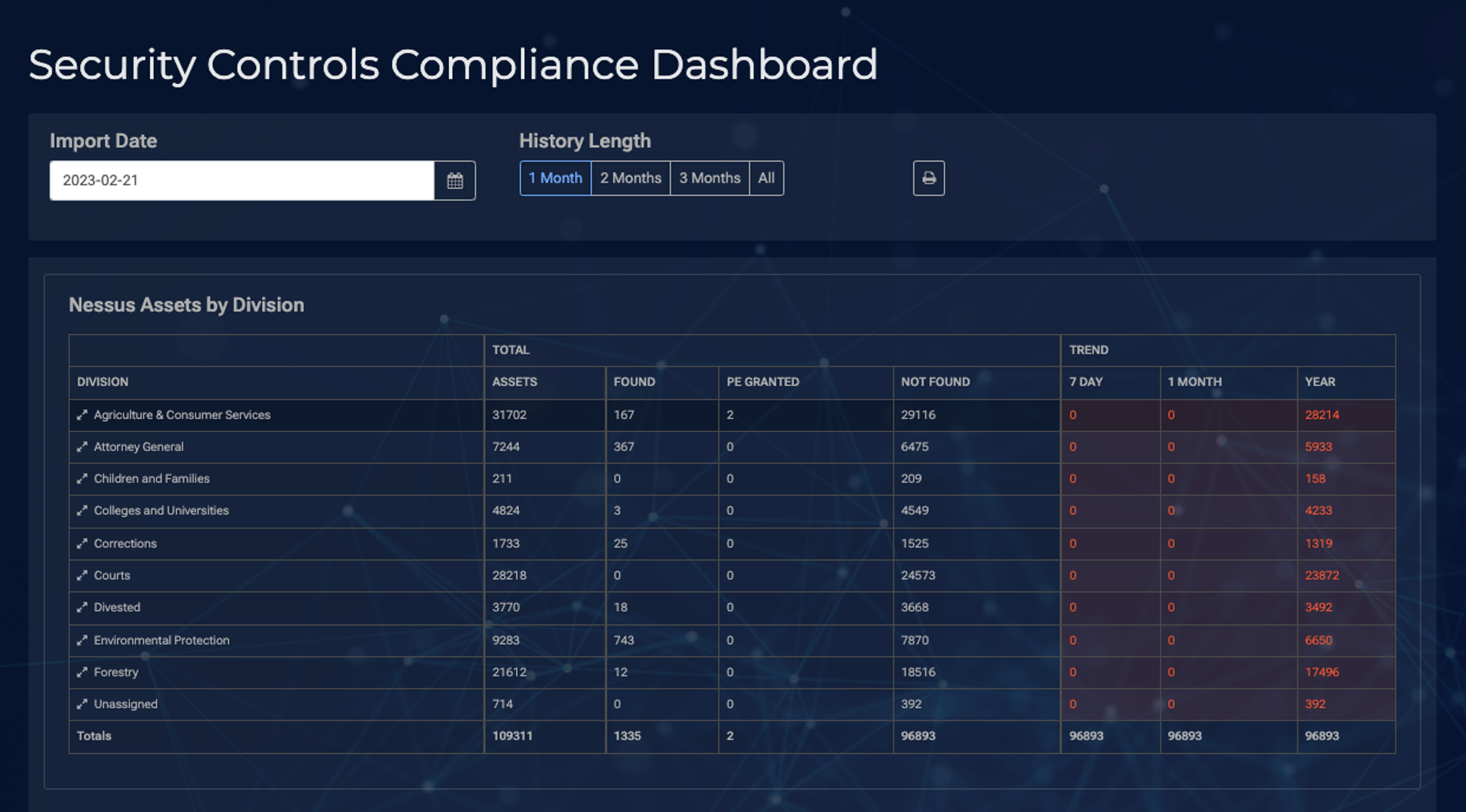
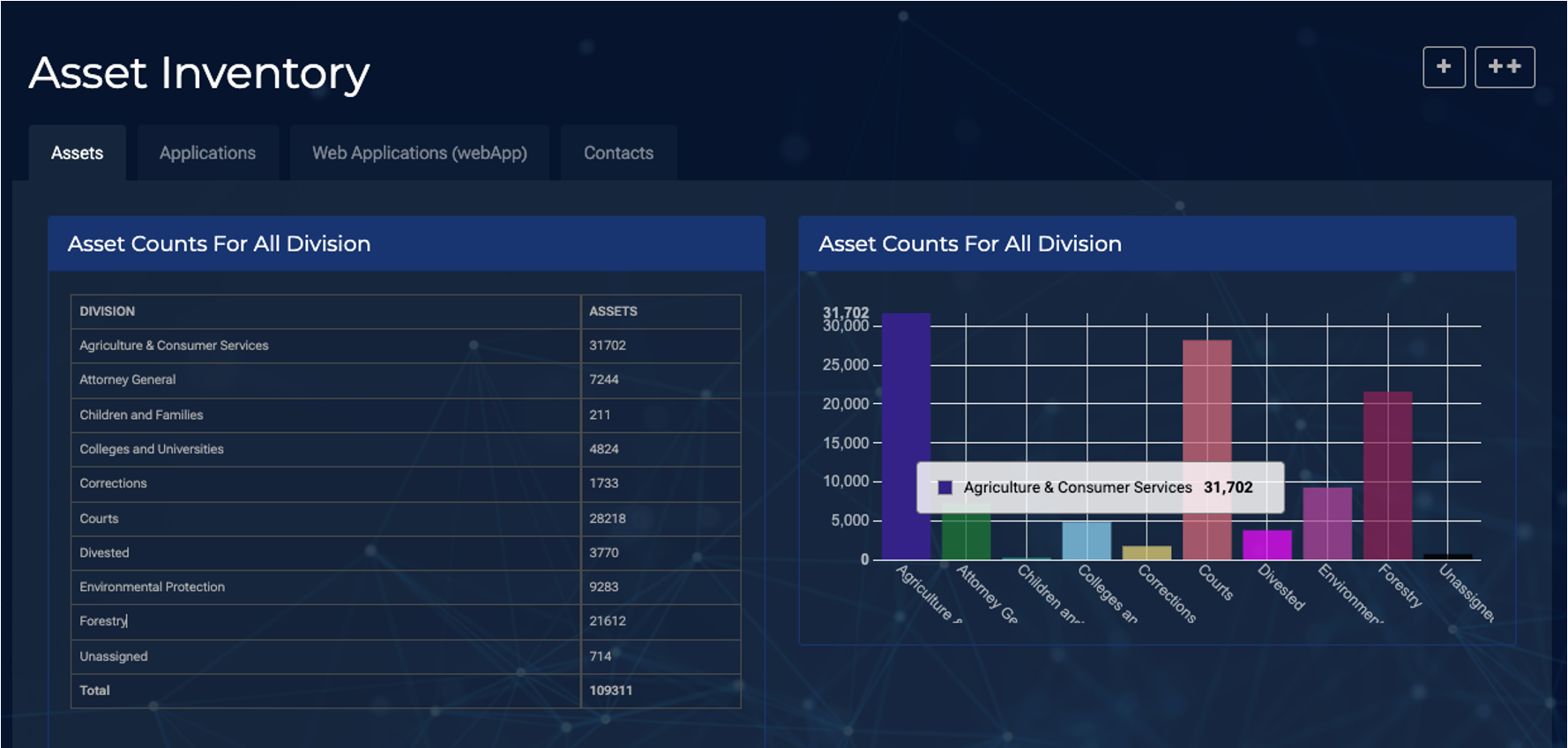
With its full asset management capabilities, the Connective Platform enables organizations to gain complete visibility and control over their digital assets. From hardware devices to software applications, every component is tracked and monitored to ensure a secure and compliant environment. This level of asset management empowers organizations to make informed decisions regarding their cybersecurity posture and resource allocation.
Identity and access management is a crucial aspect of any robust cybersecurity strategy. The Connective Platform incorporates advanced features, allowing organizations to efficiently manage user identities, control access privileges, and enforce strong authentication protocols. By implementing strict Identity policies, organizations can mitigate the risk of unauthorized access and insider threats, strengthening overall security defenses.
User access review is another vital component offered by the Connective Platform. It enables organizations to regularly evaluate and validate user access rights, ensuring that permissions are aligned with job roles and responsibilities. By conducting comprehensive user access reviews, organizations can minimize the potential for privilege misuse and maintain a robust security posture.
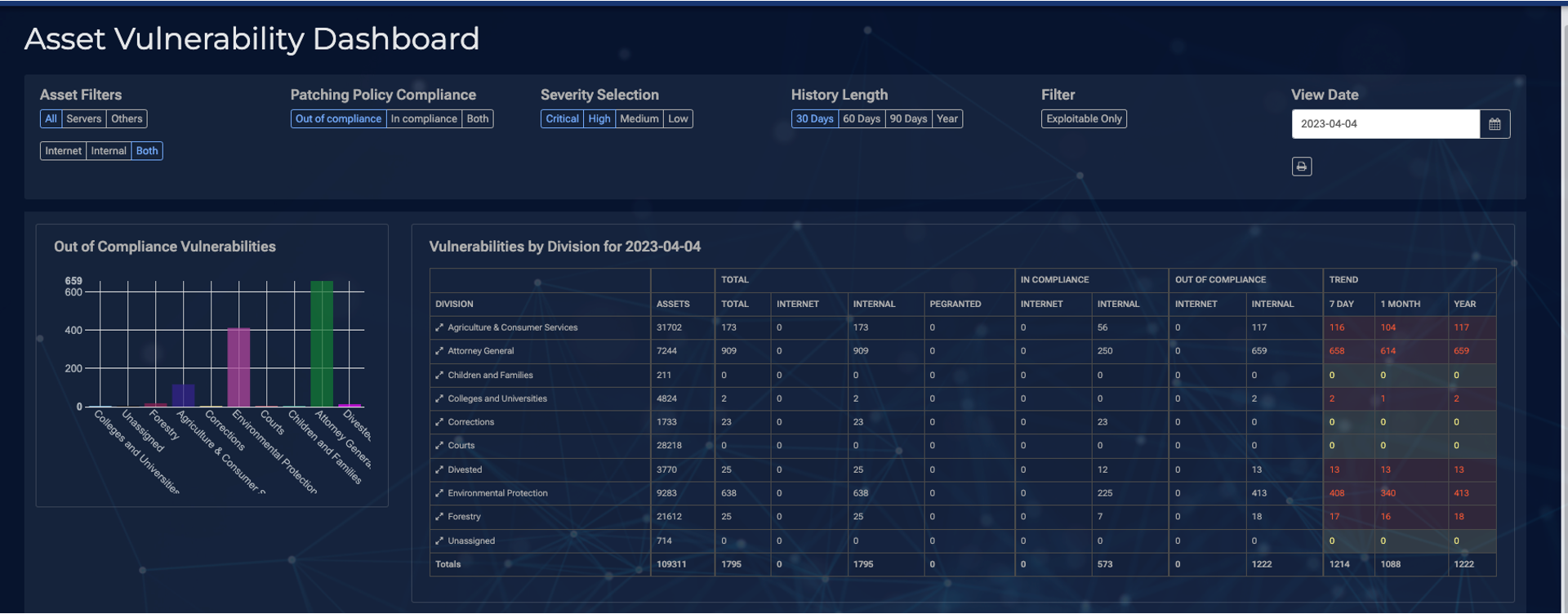
Network security is a paramount concern in today’s interconnected world. The Connective Platform provides robust network security measures, protecting organizations from external threats, unauthorized access attempts, and data breaches. With advanced firewall capabilities, intrusion detection systems, and real-time monitoring, the platform offers a layered defense mechanism to safeguard critical networks and prevent unauthorized activities.
Data protection is at the core of the Connective Platform’s offering. By implementing advanced encryption techniques, data loss prevention measures, and secure data storage practices, organizations can protect sensitive information from unauthorized disclosure or tampering. The platform ensures data privacy and integrity throughout the entire data lifecycle, maintaining compliance with regulatory requirements and industry standards.
.
The Connective Platform is designed with future-proofing in mind. It allows for seamless connectivity and interoperability between diverse cybersecurity tools, enabling organizations to leverage the benefits of existing investments while integrating with emerging technologies. By consolidating data from various sources and systems, the platform provides a unified view of the cybersecurity landscape, facilitating proactive decision-making and strategic planning.
The Connective Platform empowers organizations to take control of their cybersecurity program and protect their critical assets effectively. With its comprehensive features, intuitive dashboard, and future-ready architecture, the platform is a trusted partner for enterprises worldwide, ensuring robust security and peace of mind in an increasingly complex digital world
Our unique cybersecurity tool, The Connective Platform, provides the solution for company systems, small and large, across the world to face emerging cybersecurity challenges.
Consolidation of existing products into a single normalized view, eliminate manual processes
Streamline Executive, Shareholder and Business leader communication
Consolidated asset views for multiple teams across the organization, querying consolidated asset inventory.

Full visibility into all assets under an organization’s control
Interoperability of existing cyber tools maximizes investment and enables auditability integrity
Quicker audit compliance reporting, visibility on shadow IT organizations, where IT lacks governance and control
About Us
Keeping up with Technology is a challenge in itself. Keeping it safe is another.
